Card testing fraud is a growing threat in the world of eCommerce. It doesn’t just hurt your revenue, it can also get your business blacklisted by payment processors.
In this guide, you’ll learn what card testing fraud is, how card testing attacks happen, and how to protect your store from being targeted.
Card testing fraud is when cybercriminals use stolen credit card numbers to check if they still work. These tests are usually done by making small transactions or failed attempts on websites that don’t have strong fraud prevention in place.
Once they find a valid card, they use it for bigger purchases or sell it on the dark web. That’s why this type of ecommer frauds is often an early warning sign of bigger attacks.
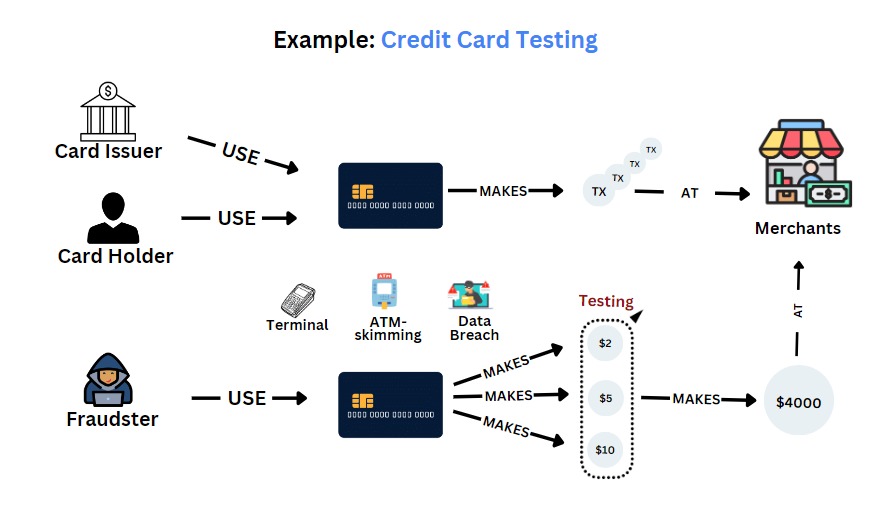
Card testing attacks are often automated and stealthy, making them hard to spot until the damage is done. Here’s how they typically unfold:
Cybercriminals obtain credit card details from data breaches, phishing schemes, or the dark web. These card numbers may or may not still be valid.
Example: An attacker buys a database of 10,000 stolen credit cards for $50 online. They have no idea which ones are still active.
Attackers use automated bots or scripts to test the cards quickly to simulate purchases on vulnerable websites. They often try small, low-risk transactions (like $1 or less) to avoid triggering fraud alerts.
Example: A Shopify store without CAPTCHA gets 500 attempts in 10 minutes, all trying to purchase a $0.99 sticker.
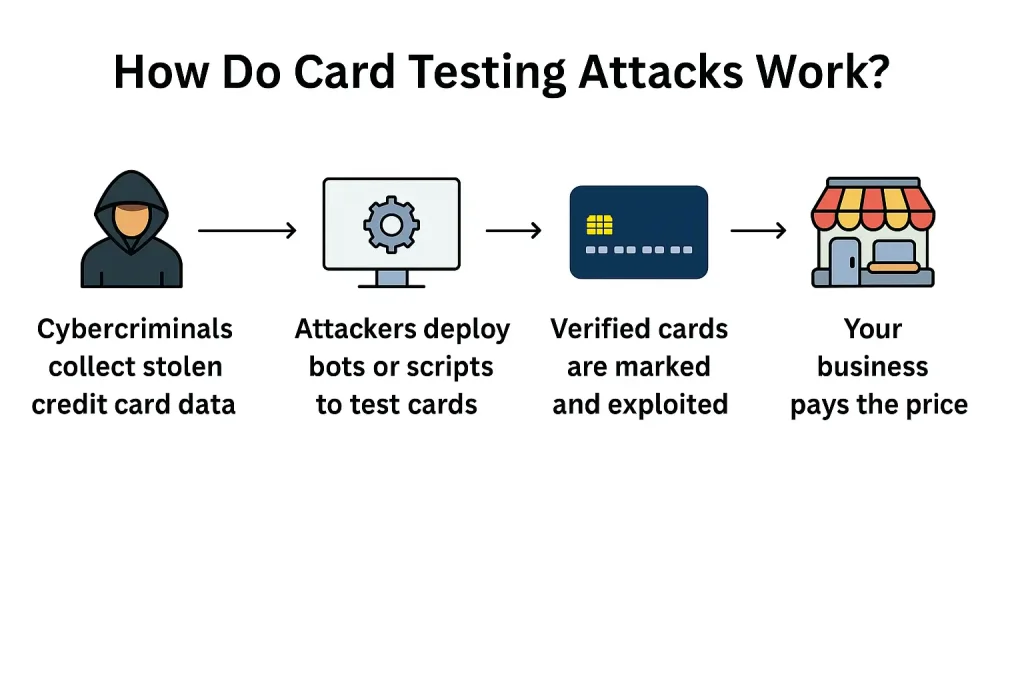
If a card passes the test, meaning the transaction goes through, it’s marked as “live.” The attacker will either use it for big-ticket purchases elsewhere or resell it at a higher price on dark web markets. Meanwhile, your store is stuck with suspicious charges, potential chargebacks, and processing fees, even for failed attempts.
Card testing doesn’t just cost you money, it hurts your reputation. Payment processors may charge more per transaction or flag your store as high-risk. If customers notice strange activity tied to your store, they could lose trust and stop buying altogether.
Card testing might seem harmless at first, after all, no products are actually stolen. But the hidden costs add up fast. Every failed transaction still incurs processing fees, and if hundreds of test attempts hit your store, that’s real money lost. Worse, if those attempts lead to chargebacks from cardholders who never authorized them, your chargeback rate can spike. That damages your standing with payment providers.
Eventually, your store could be labeled as high-risk or even get banned from platforms like Stripe or PayPal. And once you lose access to trusted payment gateways, recovering customer trust or even resuming operations becomes an uphill battle.

Card testing often starts quietly, but it leaves digital footprints you can spot if you know what to look for. Here are the key warning signs.
One of the earliest red flags is a sharp increase in low-value transactions, usually $0.50 to $5. These are “test” payments used by bots to verify card activity without drawing attention.
If you notice a wave of small purchases that don’t match typical customer behavior, chances are your site is being targeted. These transactions often fly under the radar if you’re not actively monitoring trends.
When dozens or hundreds of stolen cards are submitted, most will fail. That creates a sudden spike in declined transactions within a short timeframe.
This puts pressure on your payment processor relationship, as a high decline rate can signal fraudulent activity, even if no real purchases go through.
Legitimate cardholders may notice suspicious charges and file disputes. Even small test payments can trigger chargebacks if the customer didn’t approve them.
Too many chargebacks can ruin your store’s reputation with banks and lead to penalties, withheld payouts, or account freezes.
If your payment logs show multiple attempts using cards from unusual countries or with random patterns, that’s a red flag. Bots often run through bulk card lists without geographic logic.
Frequent mismatches in billing addresses, names, or IPs are strong indicators that you’re being used as a testing ground, not a real shopping site.

You can’t stop attackers from trying, but you can make your store much harder to target. Here’s how to block card testing before it causes damage.
Adding CAPTCHA to your payment pages helps block automated bots from flooding your checkout with fake transactions. It’s a basic but powerful way to make card testing attacks less efficient and more frustrating for attackers.
In addition to that, rate limiting adds another layer of protection by restricting how many payment attempts can be made from the same IP address within a short time. This combination makes your site much harder to exploit with brute-force scripts.
One of the most effective ways to fight card testing is by using a dedicated fraud prevention tool like Blockify. Built specifically for Shopify merchants, Blockify helps detect and block suspicious behavior automatically before it turns into financial loss.
It monitors your checkout flow in real time, flags high-risk activities like rapid-fire transactions, bot-driven checkouts, and mismatched payment details. Best of all, it works quietly in the background without slowing down your store or disrupting genuine customers.
If your store starts receiving payment attempts from countries you don’t serve, or from IPs linked to bot networks, it’s time to block them. Most eCommerce platforms or security tools allow IP filtering and geo-blocking directly from the admin panel.
As a result, you can reduce exposure to bot-based card testing campaigns, which often originate from specific regions or rotate through compromised proxies.

Regularly checking your payment logs helps you catch unusual activity early, such as sudden spikes in failed payments or repeated attempts from the same user agent. Don’t wait until chargebacks show up to realize something went wrong.
To stay proactive, you should also set up alerts with your payment provider or fraud tool so you’re notified when suspicious behavior is detected, giving you time to react before damage spreads.
Address Verification System (AVS) ensures that the billing address entered by the buyer matches what the card issuer has on file. When paired with CVV verification, this method blocks incomplete or suspicious payment attempts.
Since most attackers don’t have full cardholder data, these checks act as a strong gatekeeper, helping your store reject fraudulent charges before they go through.
In 2022, Stripe, one of the world’s largest payment processors, faced an alarming surge in card testing activity across its platform. Fraudsters were sending millions of low-value or zero-dollar transactions to merchants’ stores, aiming to validate stolen credit card numbers without being detected.
At the height of this wave, Stripe reported that its fraud prevention system, Radar, was blocking over 20 million card testing attempts per day. To help protect merchants, the company upgraded its detection models and urged users to implement stricter anti-bot and payment flow protections. You can read more about how Stripe responded to this threat in their official newsroom report.
Final thoughts
Card testing fraud may not steal your products, but it can quietly drain your business. By understanding what it is and how card testing attacks work, you can take the right steps to block fraud before it escalates.
Using a smart app like Blockify makes it easier than ever to detect and block card testing before it causes real harm.
Don’t wait until it’s too late, lock your checkout down today!